Absolute privacy
⚠CAUTION: Please read carefully before encrypting your books. You risk losing your data by locking yourself out of it.
⚠WARNING: We’ve seen some competitors claiming they offer users this level of privacy. Please test this by asking them: Is my clear (unencrypted) encryption key ever leaving my device? Can you use it to decrypt my data directly on your servers? If the (honest!) answer is yes, then they don’t really offer such levels of privacy as us. It’s as simple as this.
In addition to industry-standard practices outlined in the Privacy section, which you’re encouraged to read, you benefit from what we call absolute privacy for your books. This is accomplished through what’s known as zero-knowledge encryption: your data arrives to our servers already encrypted with a key we have zero knowledge of.
What is absolute privacy?
Absolute privacy ensures no one in the world except yourself can read your books, until you’re ready to publish.
This is accomplished by:
encrypting your books directly on your devices before sending them to the cloud
using passwords that only you know and never leave your devices
the passwords are not stored anywhere outside of your devices
The hole in data privacy
While almost every web app during these paranoid times provides a reasonable degree of user data privacy, there is one nasty hole in the middle of it.
If you entrust your data to an online application that does not provide the option to encrypt your data on your device, with a password that never leaves it, isn’t stored anywhere outside of your device, and only you know, then your data can be read by their staff with database read privileges, and that’s a fact.
With normal web applications, their database administrators and other authorized staff can read your data by simply looking in the database. Absolute privacy resolves precisely this.
When you write something in a note-taking app like Evernote, authorized Evernote staff can read it. When you write a document in Google Docs or save one in your Google Drive, authorized Google staff can read it if they choose to. You may only now realize this fact, but it’s a fact nevertheless. These two examples are big players that can be held accountable, and also offer to some degree the possibility for you to locally encrypt the data they hold on your behalf with a password that they do not store, and so they can’t use to decrypt and read your data.
Instant messenger apps, such as WhatsApp or Signal do a much better job of this, with end-to-end asymmetric encryption, but these are not apps that deal with document management — for example, you can’t edit a message you’ve already sent (except delete it altogether).
The vast majority of web applications out there don’t offer anything remotely similar, and therefore you must accept that staff with legitimate access to the database can simply read your data in there.
This is not that bad, since it’s standard practice, and company staff is legally bound to protect and never disclose user data. Nevertheless, people (and especially writers) may be uncomfortable with this state of affairs.
The case for absolute privacy
Books are meant to be read. Well, most are. However, you may entrust Novelitist with sensitive personal data, such as intimate journals and notes (remember that you can use Novelitist as a writer’s notebook as well, easily — in fact, you can forego your note-taking app subscription altogether, and just use Novelitist for note taking).
There are a few situations where you benefit greatly from absolute privacy as described above:
You want to protect sensitive, personal writings, that are not meant for publishing, ever: intimate journals, personal stories and accounts, research material, original ideas you value and would like to keep from prying eyes, etc.
You want to make absolutely sure there are no premature “leaks” of your work — whether you’re an established writer, where that really matters, or a rising star.
You just want to enjoy total peace of mind about your data not being readable by anyone else but yourself, until you deliberately make it public.
You’re just really conscious about your content being read by an uninvited third-party.
How absolute privacy works
The core concept boils down to this: your book is encrypted on your device with a password that only you know and that never leaves your device. Then when the book is sent to our cloud, it’s already encrypted, and saved in the database as such. Now anyone with access to the database will only see gibberish, and unless they get the password from you (since we don’t store it anywhere), they’ll never be able to read it.
What gets encrypted
When you opt for absolute privacy for a book, you fully encrypt:
The book itself in our database
The section snapshots you’ve taken and we store
All backups of that book in our cloud
NOTE: cover images, although not encrypted, are not displayed in your library (don’t freak out). That’s because the encrypted books don’t expose the cover image URL and so the cover image can’t be rendered in the library.
What’s not encrypted
Some things are out of scope for absolute privacy, and you need to be mindful of them:
Any images you upload are not subject to absolute privacy, and are not encrypted.
Your custom/ignored dictionary words for spelling purposes
Additionally, as a rule, anything that lives on your devices is decrypted, thus entirely readable: local backups in your browser, section versions, file backups, etc. They need to be decrypted, so that you can read and use them locally. On your device, your data must be protected by your device security measures (device PIN, biometrics, device storage encryption and so on). Absolute privacy strictly refers to what happens with your data outside of your devices.
Therefore when you download a file backup of an encrypted book on your device, that file backup won’t be encrypted (this is your escape hatch if you forget an encrypted book’s password — see below). It’s up to you if you want to encrypt that file on your device by other means.
How to encrypt a book
We’ve made encrypting your books on your devices, for absolute privacy, as easy and painless as possible. This works for existing books as well as newly created ones, and it’s entirely reversible (as long as you know the password). It’s a simple, seamless process that you can perform on any of your devices.
Step 1: Open an existing book or create a new one
Either open an existing book from your library, or create a brand new book, which will automatically open it.
Step 2: Click the lock icon above your left sidebar
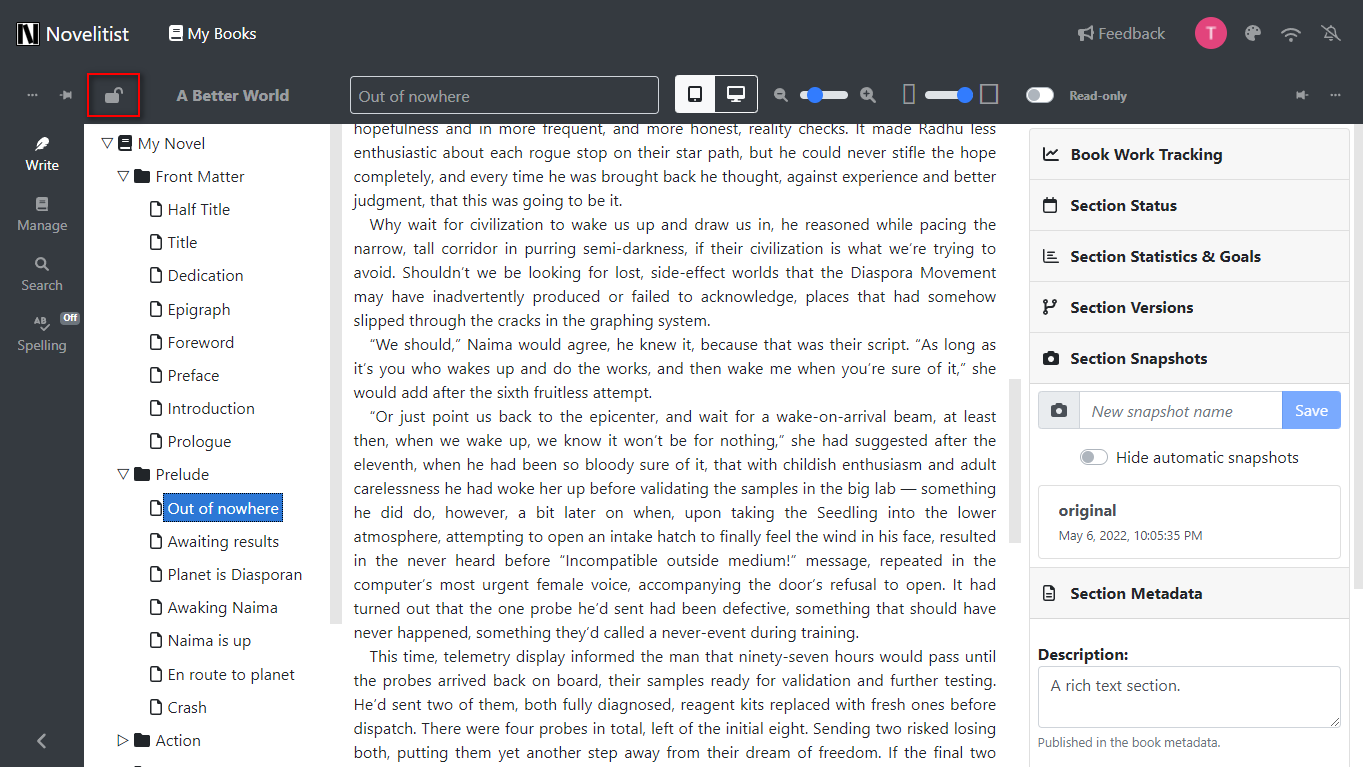
This will bring up a dialog where you can set up absolute privacy via encryption on your book. This is what it looks like for an unencrypted (ordinary) book:
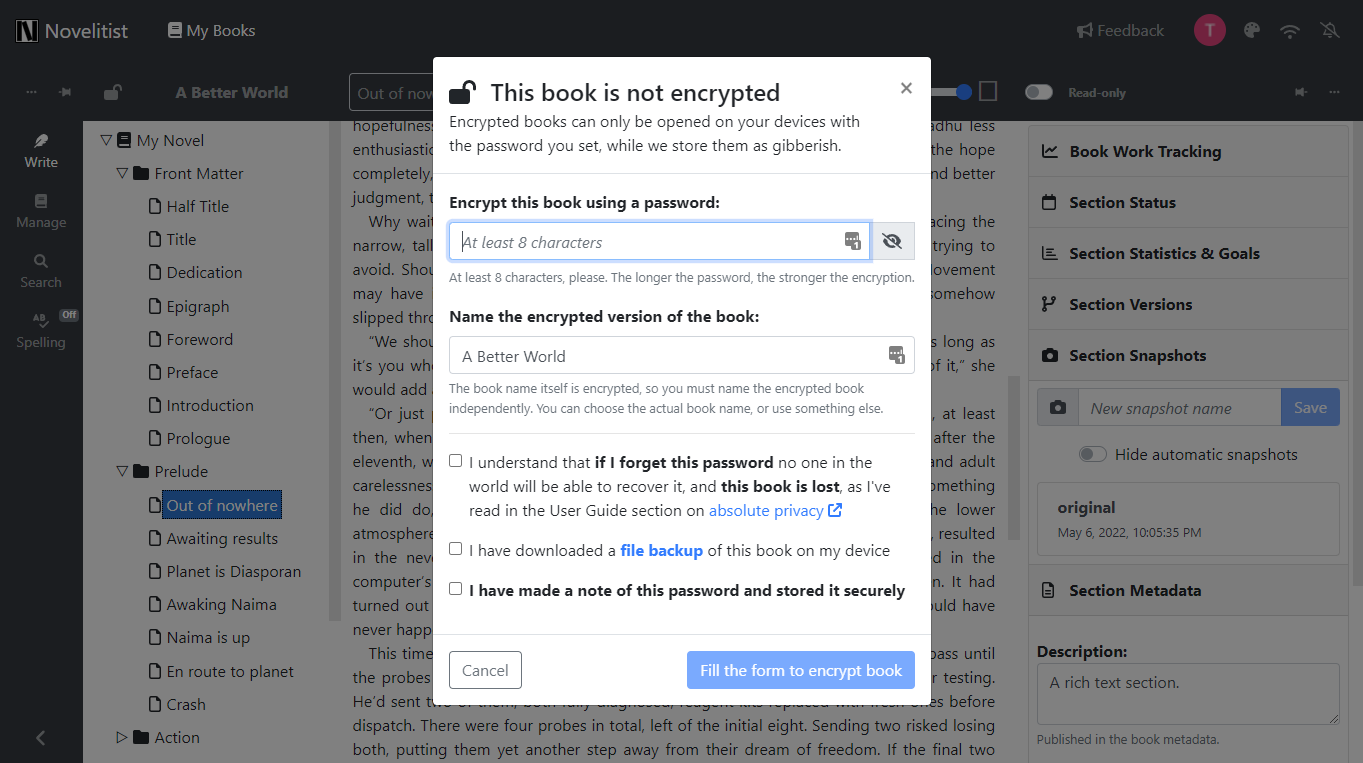
Follow the setup instructions, and you’re done — your book is now encrypted and can only be read by you, when you decrypt it on your devices with the password you’ve set. No one in the world, including our staff with database access, can read it now. Never share your password with anyone, including Novelitist staff! We’ll never ask for it. If it appears that we do, contact us immediately, as you may be a victim of phishing or other bad behavior.
Use a strong password. The stronger the password, the harder to guess the encryption key. A length of ten characters is the minimum requirement we enforce, but make it as long as you can, make it a passphrase. Cracking a good password may take centuries, while cracking a weak one (short, predictable, using common words, etc.) may take mere seconds or minutes. Make a note of this password, and don’t lose it! If you forget it, you lose your book for good, unless you’ve previously saved a file backup of it.
A word on the “encrypted book name”: since the entire book is encrypted, including its name, you need to provide an identifier (name) for the encrypted version of the book, so that you’ll know what to input the password for when you decrypt it on your device. This new name is not encrypted, therefore visible in our database. You may use the actual book name, or choose any other decoy name, it’s up to you. This will then be the book name you (and everyone else) will see before decrypting the book (which only you can do).
Step 3: Manage your encrypted book
Once you’ve encrypted your book, click on the lock icon again (it now shows as a closed lock of a different color).
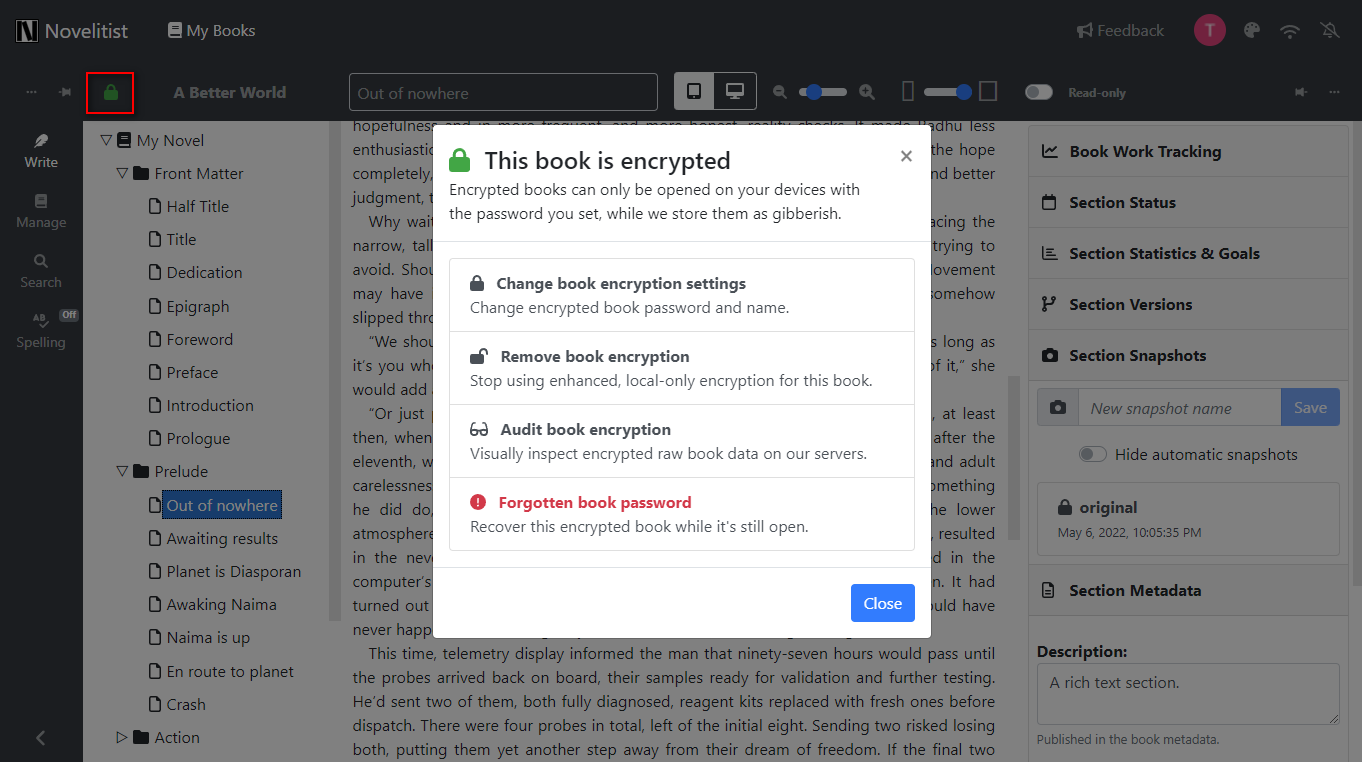
This brings up a dialog where you can:
Change the book’s encryption settings: the encryption password and/or the book visible identifier (name).
Remove the book encryption entirely: this turns the book back into a normal, unencrypted book.
Audit the book encryption: this is provided for your peace of mind — details below.
Recover the book while you still have it open, if you think you’ve forgotten its password.
Everything here is self-explanatory and will allow you to manage your encrypted book with minimal friction.
Step 4: Auditing book encryption
For your peace of mind, you can at any time query our storage for the raw book data, exactly as it’s stored on our servers, using the dialog above (click “Audit book encryption” and follow the instructions). This raw data includes all the book data, with the section snapshots and cloud backups as well, and it’s what anyone in the world would see when looking at it in our cloud.
You will be presented with a raw book data dump, as below:
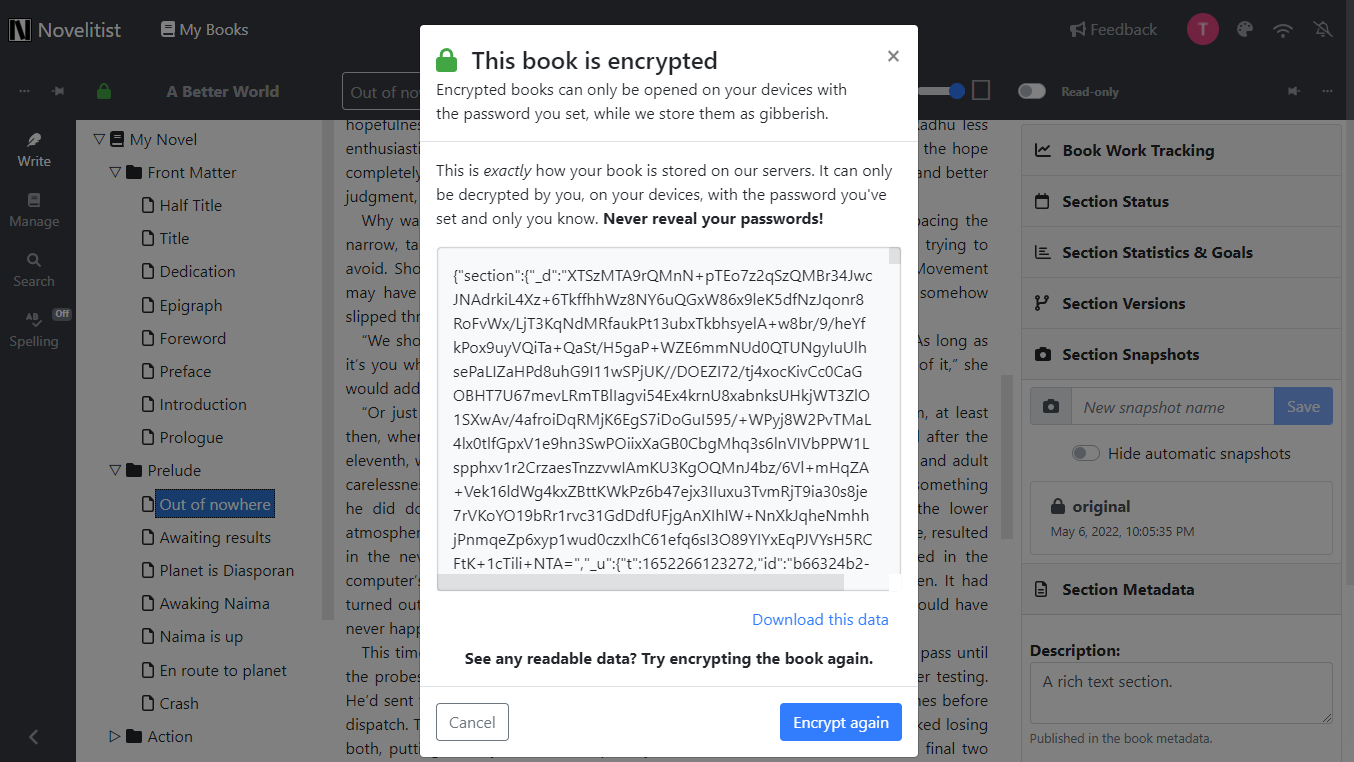
The goal of this audit is to determine that none of your data (except the encrypted book name) is readable, i.e., it looks like gibberish, indecipherable.
The app runs an audit of this data in your browser, and can tell you if some of the data is readable when it shouldn’t. However, only your full visual inspection of it can provide the definitive verdict, since that’s the whole point of this audit — for you to see with your own eyes how your data is stored remotely.
Passed audit
If you can’t read any of your data in there, that means no one else in the world can, be they our database administrators or other authorized staff. That means the book encryption is comprehensive. This is the usual situation you’ll encounter.
Failed audit
If you can read some of your data in raw form, because it’s intelligible, that means book encryption is incomplete, which may sometimes happen when encrypting on different devices, due to sync issues, or an unstable network connection. Fixing it is as simple as re-encrypting your book (just click “Encrypt again”). You can even use the same password, it doesn’t matter, what matters is that the entire book data is again downloaded to your device, encrypted with the password only you know, and then re-saved as such in the cloud.
NOTE: For large books with many snapshots and backups, the raw data is too large to display in your browsers. You will be prompted to download it as a text file, which you can then open and audit on your device like any other file. The rest works just the same.
Absolute privacy is opt-in
Any Novelitist writer can choose to encrypt their books like this, thus achieving absolute privacy for that book. You may want to do this only for certain books, and that’s fine. That’s what it means that this is an “opt-in” feature — you can use it on some of your books, all of them, or none.
You can also opt in and out of absolute privacy for any book, i.e., once you’ve decided to encrypt a book, you can always reverse it, and vice versa.
Your book is still protected from outsiders by user account authentication and the default cloud encryption, even if you opt-out of absolute privacy. Absolute privacy is just the cherry on top of the entire privacy cake.
Absolute privacy pitfalls
Absolute privacy is a beautiful, empowering concept. Like with most beautiful and empowering concepts, there are some pitfalls to consider. Here are the most significant:
If you lose your password, you’ve lost your book
With the great power of keeping your writing absolutely private comes the great responsibility of being the only one able to decrypt and read your data.
Since only you can decrypt your books, no one can help you recover them if you lose your encryption passwords.
Since we don’t know or store your book encryption passwords anywhere, if you forget them, there is no way we can help recover your lost encryption passwords — and that’s the whole point of absolute privacy! Without the correct password, the book remains forever encrypted, and therefore useless. You’ve essentially ransomware’d yourself, yet no matter what you’d pay, there’s no one to pay it to in exchange for the password, since you represent all parties here.
To sum this up: DO NOT FORGET YOUR BOOK ENCRYPTION PASSWORDS!
Data corruption
In the real world, things can, and will, go wrong. Internet connection is sometimes lost, your device sometimes dies due to a depleted battery, or freezes after a system error, and sometimes an electrical outage shuts down your computer. If that happens during the process of encrypting or decrypting a book, there’s a risk of incomplete encryption or decryption, which may result in the data becoming unreadable, with or without the password, and therefore the book is lost. This may happen exceedingly seldom, but it may nevertheless.
Avoiding absolute privacy mishaps
Fret not, for there is a counterpoint to the doom and gloom above. Ensuring you don’t lose your encrypted book even if you forget your password or the book gets corrupted is in fact quite easy, but it’s also your responsibility:
Backup your encrypted book as a file on your device as often as possible! Restore it from the file backup if you forgot the password.
The file backups on your device are always unencrypted (since they live on your device). The more recent the file backup, the less data you’ve lost when you’ve forgotten an encrypted book’s password.
So forgetting an encrypted book’s password is not the end of the world, but only provided you have a recent file backup of it. If you don’t, it is the end of the world for sure, at least for that book.
If you have a file backup of the encrypted book you’ve forgotten the password for, the book can be easily recovered:
Delete the book from Novelitist
Restore the file backup in your possession
Re-encrypt the restored book if you wish
If you don’t have said file backup, all is lost, and there’s no recourse, by the very nature of absolute privacy.
Nagging password prompts
This comes with the territory. Since your encryption passwords are not stored anywhere, you’ll have to input a book’s password every time you open it on your device. You only have to provide the password once per session and book, and after that everything continues as normal. If you refresh the page or you open another book, you’ll be prompted for the password again.
Performance
Constantly encrypting and decrypting data on your devices does entail a performance hit, which may not be an issue on faster devices, like modern computers, but noticeable on slower devices, like older smartphones.
It’s entirely up to you to assess this privacy-performance trade off. In this light, you may choose to leave certain books unencrypted.
Trust points
Trust can never be entirely encoded in the machine. There is always a human side to it that simply cannot be made algorithmic. No matter how tight and prohibitive a security system is, at some point during that interaction we humans have to trust each other the old fashion way, based on incentives as old as our species.
As a matter of course, we entrust countless online systems with our data, which is stored in data centers often on different continents, based on the mutual understanding and agreement that 1) we care deeply about our data, and that 2) its stewards manage it in good faith. Our incentive is that we need that data stored online for availability everywhere we go. The businesses’ incentive is, well, retaining our business.
In the particular case of our absolute privacy implementation that we provide to all customers (writers), you need to make a leap of faith, and trust that:
Novelitist will never allow your book encryption passwords to leave your devices, and therefore won’t store them anywhere else
The raw book data provided for your direct encryption audit is exactly what Novelitist stores in the cloud
In our opinion, considering the vast online privacy landscape and its tremendous challenges (and failures), this is a very reasonable leap of faith to make. Were we planning any mischief with your data, we would have never undertaken the considerable effort to implement what we call “absolute privacy,” for your exclusive benefit. It simply wouldn’t have made any sense to add something like this on top of industry-standard practices that we already follow.
We are in the business of serving writers and their needs, including that of absolute privacy. Our reward is retaining your business. That’s our incentive. It dictates that we honor your leap of faith accordingly, by keeping our side of the agreement with utmost stringency.
Finally, a technical word on encryption
We’ve left this for the closing of this topic, as it gets a bit technical and it has little relevance to you, the writer.
The only relevant things for you to know on this topic are that:
strong encryption is the basis for achieving absolute privacy for your book
you need to use a strong password (passphrase)
With that in mind, you can skip reading the rest of this chapter.
We encrypt your books directly on your devices using a strong key derived from a password of your choice. Long passwords (passphrases) make the encryption key exponentially harder to guess by an attacker, so make sure to choose a password as long as possible. This is an important first step towards securing your book. While cracking a good password takes centuries or millennia with the current technology, cracking a weak one takes hours at most.
We use validated algorithms with a 256-bit key derived from your password. With the current technology and with the technology of the foreseeable future, realistically, cracking 256-bit encryption by brute force takes trillions of years to achieve (that’s significantly more than the age of the Universe itself, which is “only” 15 billion years). That is to say that 256-bit encryption of a long enough string is virtually unbreakable for all intents and purposes.
Your encrypted books are protected by the implacability of mathematics. As much as they can’t be cracked open by anyone in the world by brute force, they can be instantly revealed to those who have the password — ensure that you’re the only one who does by never revealing it to anyone. Also ensure you’re using a strong password (a long passphrase), or the encryption strength is rendered useless, since your password is easy to attack.